Secureworks® Counter Threat Unit™ (CTU) researchers investigated infrastructure and malware artifacts likely used in ongoing phishing operations targeting governmental, non-governmental organizations (NGOs), and intergovernmental organizations (IGOs) based in the United States, Ukraine, and the European Union. The missions of these organizations include anti-corruption activism and conflict mediation in Ukraine as well as disinformation awareness in the European Union.
On May 26, 2021, CTU™ researchers identified two Cobalt Strike Beacon samples that used command and control (C2) servers at dataplane . theyardservice . com and worldhomeoutlet . com (see Figure 1). At analysis time, these domains resolved to 83 . 171 . 237 . 173 and 192 . 99 . 221 . 77, respectively.
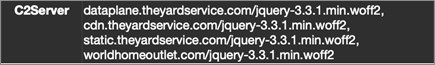
Figure 1. Cobalt Strike Beacon configured to use C2 server theyardservice . com. (Source: Secureworks)
Analysis of the theyardservice . com domain revealed multiple URLs containing the “usaid” subdomain, a reference to the United States Agency for International Development (USAID). Shodan historical records for 83 . 171 . 237 . 173 show redirects to USAID's main website at https: //usaid . gov on port 443 (see Figure 2). This activity is likely part of a USAID-themed phishing campaign.
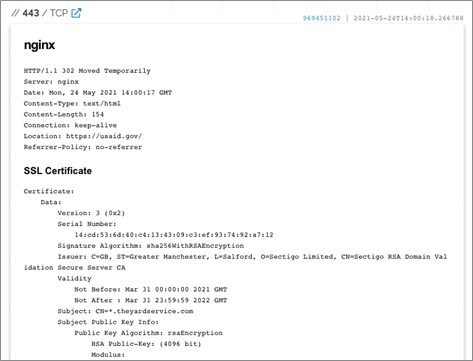
Figure 2. HTTPS queries to theyardservice . com redirect to USAID website. (Source: Secureworks)
The URLs identify specific targets based on the email address appended to the URLs. The targets include the U.S. Atlantic Council, the Organization for Security and Co-operation in Europe (OSCE), the Ukrainian Anti-Corruption Action Center (ANTAC), the EU DisinfoLab, and the Government of Ireland's Department of Foreign Affairs. The timestamps associated with some of these URLs indicate that the campaign is ongoing as of this publication.
These URLs yielded a set of corresponding URLs generated by the Constant Contact email marketing software. One of the Constant Contact URLs results in a HTTP 302 redirect to https: //usaid . theyardservice . com/d/<emailAddress>, where <emailAddress> is the final parameter value in the Constant Contact URL and the link's recipient. The C2 server responds with a 21 kilobyte ISO file named ICA-declass.iso.
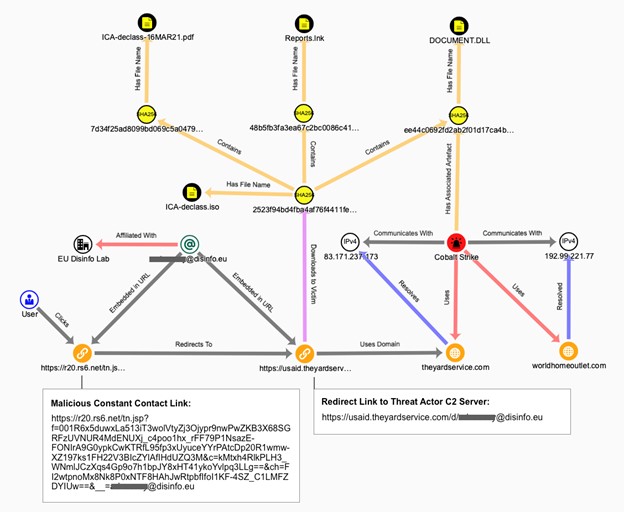
Figure 3. Constant Contact link redirects to threat actor C2 server and malware download. (Source: Secureworks)
The downloaded ICA-declass.iso ISO image file reveals three files when opened: ICA-declass.pdf, Reports.lnk, and Documents.dll. The DLL file is a Cobalt Strike Beacon executable (see Figure 4).
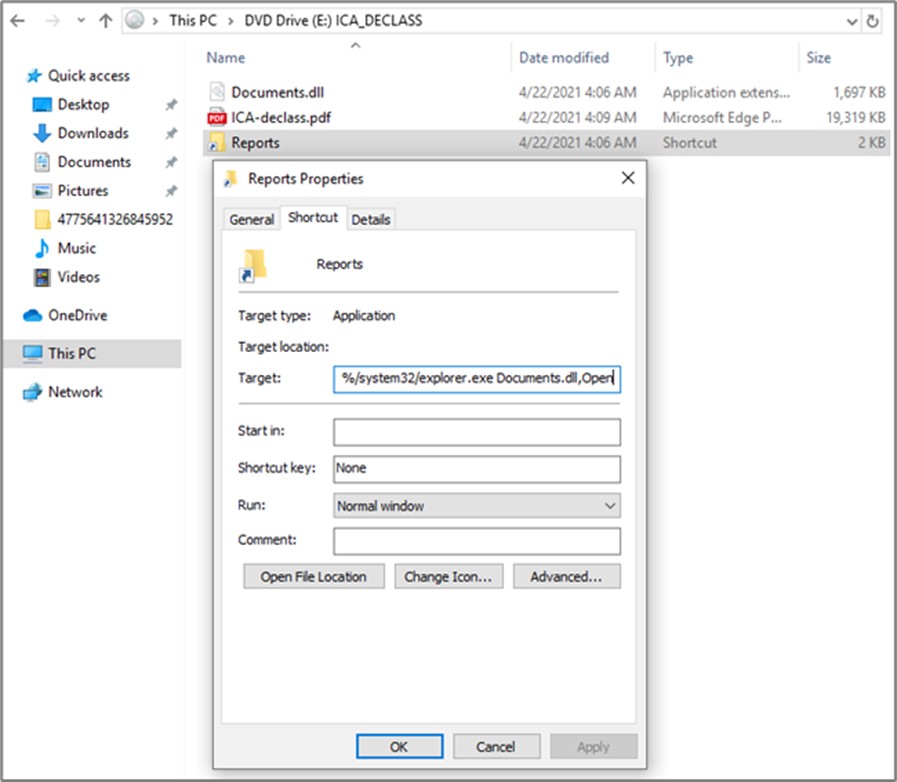
Figure 4. Contents of ICA-declass.iso. (Source: Secureworks)
ICA-declass.pdf is a benign lure document titled “Foreign Threats to the 2020 US Federal Elections.” It is a copy of a declassified and released U.S. intelligence community assessment. Reports.lnk launches Windows File Explorer and executes Documents.dll. The Cobalt Strike Beacon then attempts to connect to one of the four URLs defined in its C2 configuration.
On May 25, a security researcher identified a malware sample associated with the two phishing domains. They also provided a screenshot (see Figure 5) of what is likely an original USAID-themed phishing email sent to a target. The hyperlink associated with the “View documents” button is likely the malicious Constant Contact URL customized for that target.
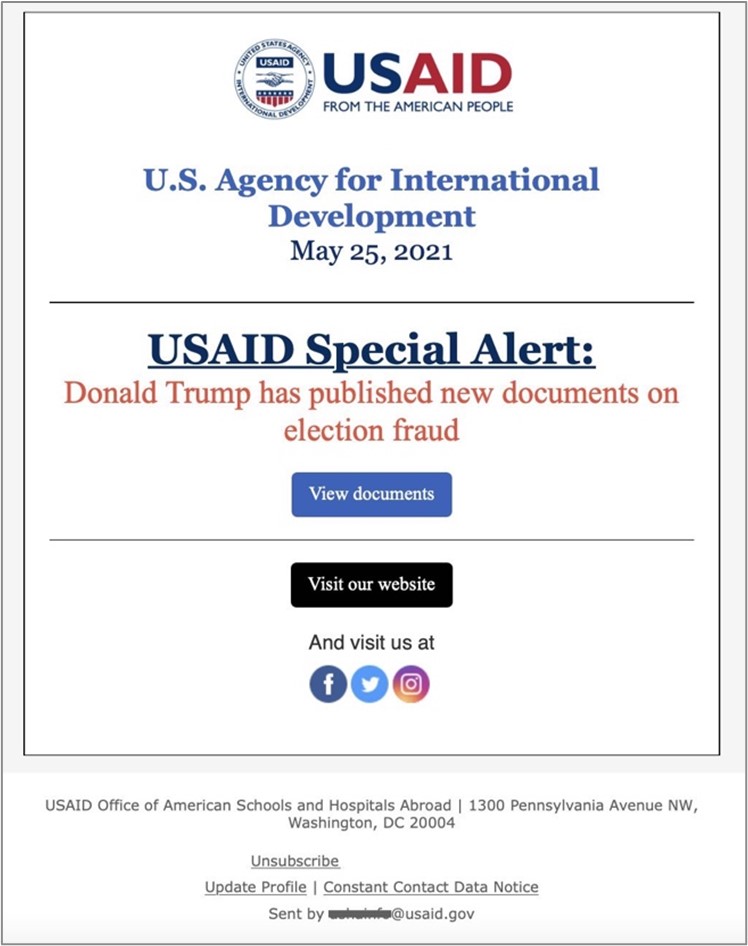
Figure 5. USAID-themed phishing email. (Source: Twitter, @ScarletSharkSec)
The very narrow and specific set of email identifiers and organizations observed by CTU researchers strongly indicate that the campaign is focused on U.S. and European diplomatic and policy missions that would be of interest to foreign intelligence services. Based on the identified targets, CTU researchers assess with low confidence that a Russian government-sponsored threat group may be responsible for this campaign. Third-party researchers attribute this campaign to the Russia-based IRON RITUAL threat group (also known as NOBELIUM and APT29). IRON RITUAL has been linked to the SUNBURST malware used in the SolarWinds supply chain attack.
Organizations whose missions make them likely targets for this campaign should be vigilant for USAID-themed phishing emails and monitor their networks for activity linked to the malware and infrastructure associated with this campaign. As a general security practice, all organizations should train employees to recognize and report phishing attempts.
To mitigate exposure to this malware, CTU researchers recommend that organizations use available controls to review and restrict access using the indicators listed in Table 1. Note that IP addresses can be reallocated. The domains and IP addresses may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
| theyardservice.com | Domain name | Cobalt Strike C2 server |
| worldhomeoutlet.com | Domain name | Cobalt Strike C2 server |
| 83.171.237.173 | IP address | Cobalt Strike C2 server |
| 192.99.221.77 | IP address | Cobalt Strike C2 server |
| 1c3b8ae594cb4ce24c2680b47cebf808 | MD5 hash | Cobalt Strike Beacon (Document.dll) |
| 1fb12e923bdb71a1f34e98576b780ab2840ba22e | SHA1 hash | Cobalt Strike Beacon (Document.dll) |
|
ee42ddacbd202008bcc1312e548e1d9ac670dd3d86 c999606a3a01d464a2a330 |
SHA256 hash | Cobalt Strike Beacon (Document.dll) |
| 7edf943ed251fa480c5ca5abb2446c75 | MD5 hash | Cobalt Strike Beacon (Document.dll) |
| 1380d7c44efde64f471ae70563372efe18f43026 | SHA1 hash | Cobalt Strike Beacon (Document.dll) |
|
ee44c0692fd2ab2f01d17ca4b58ca6c7f79388cbc6 81f885bb17ec946514088c |
SHA256 hash | Cobalt Strike Beacon (Document.dll) |
