This blog was updated and republished on 03/05/2021.

Keeping pace with online threats can often feel like you're plugging holes in a dam with your fingers – as soon as you've got one challenge under control, another issue pops up somewhere else. As employers create more flexible work conditions (BYOD, remote workforce, etc.) and mobility increases, organizations are faced with an increasingly complex task of managing their endpoints, on and off the corporate network. This is why the ability to rapidly detect nefarious activity when an adversary has physical access to a workstation is so important. With physical access, an adversary could transfer data to a USB device, an external hard drive or mobile phone – or threat actors could use these commonplace mobility devices to infect your network with malware.
Getting to the Root of a Vulnerability
Traditional security controls like firewalls and antivirus software can alert you if you've been infected with malware – but they don't offer the visibility required to detect crucial elements in the lifecycle of this kind of breach. Without the ability see where the infection originated, your security team could be focused on treating symptoms and not the root cause.
The Secureworks® Endpoint Detection and Response (EDR) agent, included in Secureworks Taegis™ XDR and ManagedXDR, acts as a surveillance camera – it records a wide range of information about the endpoint security and can show you where a threat originated, helping you better address the source of a potential compromise and safeguard against future incidents. For example, USB drives are common workplace devices, and while they can be useful tools, they can also be convenient attack vectors for deploying malware. Traditional antivirus is ineffective against advanced threats and though Next-Generation Antivirus (NGAV) can scan these tools and is more effective at finding advanced threats, it can be difficult to implement remediation broadly without yielding false positives. Our EDR records artifacts on a Windows or Linux system that provide forensic information when a USB storage device is connected. Instead of playing whack-a-mole, reacting to each symptom caused by a vulnerability or compromise, you close the access vector completely.
Endpoint Detection and Physical Security with Secureworks
When a new USB device connects for the first time, Windows will load a module that prepares the device for use. We will record when Windows loads the device's software (or library) and will provide the time and user who invoked the activity.
![]()
Figure 1. Secureworks telemetry showing preparation for the installation of a plug and play device.
Once this library is loaded (or the software installed), Windows will start to install the driver so that it can function. The driver is what allows the USB to work – it's a low level part of the hardware that allows it to communicate with the operating system. The device's commandline tells the system what to run, and we will record the commandline for this process which will contain information, allowing us – Secureworks® threat hunters or your own security team members with access to the Secureworks portal – to identify the device by enumerating the vendor and product IDs and then how to trace back to the issue's origin. These fields are abbreviated and separated by an ampersand in the commandline.
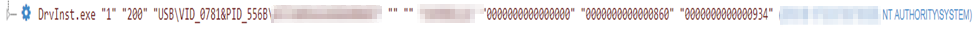
Figure 2. Secureworks telemetry showing the USB device details during driver installation.
Correlation with open source tools to identify the device with this information becomes possible. Some devices will start another instance of drivers that will list the device's vendor and product information verbatim.

Figure 3. Secureworks telemetry identifying the USB device's vendor and product name.
These artifacts will allow for a more conclusive analysis during an investigation by using information like timestamps, user identification, and device information. This is critical because USB devices can be used as the initial access vector to propagate malware. They can also be leveraged to steal data using their native functionality without the need to install malware at all. This information is indispensable when performing root cause analysis and when informing incident response. That is why this telemetry is invaluable in today's threat landscape.
Don't Let Devices Lead to Downfall
Mobility has made USB devices commonplace in the workplace and many remain unaware of the risks these seemingly benign tools present. Having tools and the right expertise to interpret and correlate the data is critical to combat issues of compromise. But be sure you're practicing strong endpoint security hygiene as well:
- Limit access to administrative privileges
- Help prevent Shadow IT by limiting administrative rights that allow employees to use programs that have not been vetted by your IT and security teams
- Implement and enforce a strict USB user policy
- There are solutions to help enforce USB policy – e.g. an Active Directory Group Policy Object (GPO) can allow read access but prevent write access, preventing it from copying information from the end user's drive
- Conduct regular security awareness training for employees at all levels
- Threat actors know they can exploit human vulnerabilities so keep security top of mind and arm your staff with strategies to prevent compromise
